Successful Business Continuity Planning “Starts at Home”

The last few months have dramatically underscored the impact of rapidly evolving cyber threats – and information security vulnerabilities – in healthcare. In mid-December, a ransomware attack on Ultimate Kronos Group “disrupted payroll for thousands of employers.” According to a recent article from NPR, the outage impacted a total of “about 8 million employees” across all industries, but “health care employers [were] hit particularly hard,” with the outage serving as “an unneeded administrative nightmare timed precisely as the omicron surge [was] hitting hospitals.” Also in December of last year (but unrelated to the cyberattack on Kronos), researchers disclosed “critical vulnerabilities” in the Log4j logging tool. Per a recent guide from HHS, “Log4j is a Java-based, ubiquitous logging tool now known to have multiple vulnerabilities, including multiple remote code execution flaws that can provide an attacker total control of a system.” While HHS notes that there had not been any major compromises in healthcare at the time when their Log4j guide was published (1/20/22), the agency warns that “the health sector remains highly vulnerable, as do other industries.”
Top 20 Countries with Most Log4j Exploit Attempts
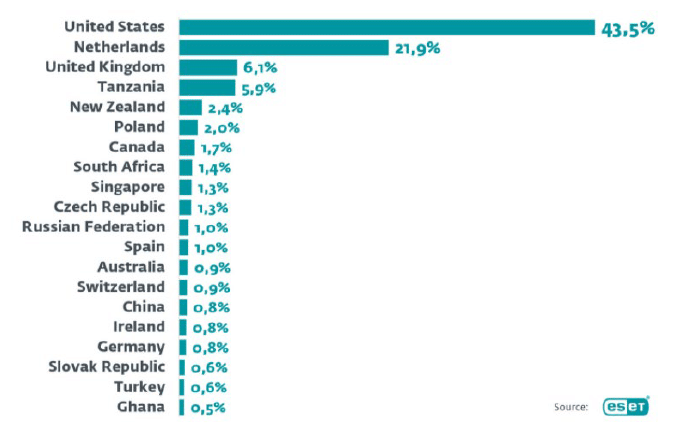
Image source: “Log4j Vulnerabilities and the Health Sector,” HHS, Jan 20, 2022
Why It Matters:
The recent news serves as an important reminder that cybercriminals are not just trying to infiltrate hospitals and health systems directly; they are also gaining access to health delivery organizations by targeting providers’ business partners. It is obviously paramount that hospitals and health systems continue to make their own information security a top priority, but it is also critical for health delivery organizations to evaluate the security posture of their vendors and trading partners as well. However, there is no way to ensure complete and total protection against ransomware and other cyber threats – and no provider organization or any third-party vendor is immune. For this reason, incident response and business continuity plans in the event of a ransomware attack are critical. Providers can (and should) try to get assurances that their vendors have proper incident response and business continuity controls in place if an outage occurs due to a ransomware attack – but that alone isn’t enough. Health delivery organizations still need to take it upon themselves to prepare for the worst-case scenario of any key system becoming encrypted by cybercriminals, regardless of whether the provider owns the product and controls the environment, or whether the provider subscribes to a cloud-based solution that is centrally hosted and managed by a third party. In other words, successful incident response and business continuity planning starts at home. It isn’t enough just to ask vendors “what is your plan” to respond to an outage from a ransomware attack or to address a newly discovered information security vulnerability; hospitals and health systems need to be able to answer “what is our plan” as well.
Related Reading
Can healthcare improve third-party vendor security, business continuity?
Incident Response – Are you Prepared for a Security Event? Scottsdale Institute Webinar
This article was originally published in Impact Advisors’ digital newsletter: The Impact Advisor 1Q2022.
























